Service Overview
When your business applications go to clouds, Identity and Access Management (IAM) and Single Sign On (SSO) becomes critical in cybersecurity. Besides using multi-factor authentication (MFA) to strengthen identity control, businesses can minimize cybersecurity risk by closing up unnecessary openings to the external world in operations.
Often in the process of digital transformation, businesses rely on collaborations with partners. However, human errors in such collaborations can leak security information and cause businesses a great loss in profit or reputation.
Akamai Enterprise Application Access (EAA) applies a zero-trust security management model. For example, it closes all ports going into a firewall and at the same time it ensures that authorized users and devices can visit only certain applications and not your entire network.
Features
● Centralized Access Management
Akamai EAA allows your business to activate access management of your business application within minutes with no extra hardware or software whether your application is deployed in a private cloud (e.g. VMware or OpenStack), a public cloud (e.g. AWS, Microsoft Azure, Google Compute Engine, or IBM Cloud SoftLayer), or on-premise.
● SAAS Integration
Akamai EAA provides seamless access to internal business applications from suppliers such as Atlassian, Microsoft, SAP and Oracle. Akamai EAA can also integrate with Okta or other SSO solutions.
● Multi-Factor Authentication (MFA)
Akamai EAA offers identity authentication through emails, SMS, or TOTP. Akamai EAA can also integrate with 2FA suppliers such as Duo Security to give you an extra layer of protection.
● Built-in Load Balancers
Akamai EAA can distribute visits to your internal business applications based on your policy after monitoring the status of your business application. This increases the reliability of your business operation.
Steps of Implementation
- Step 1: Apply for Akamai Enterprise Threat Protector (ETP)
You can get in touch with us here to apply for an Akamai EAA trial.
- Step 2: Deploy Security Connector
- Download EAA VMWare OVA
- Deploy OVA to your cloud environment
- Configure Security Connector IP
- Configure Security Connector DNS
- Configure Security Connector NTP
- Verify the network configuration of Security Connector
- Verify the network connection of Security Connector
- Verify the registration of Security Connector
- Step 3: Configure Identity
○ Add new accounts and passwords using Akamai EAA’s Cloud Directory
○ Create an Organizational Unit (OU) and authorizable accounts through your existing AD/LDAP
- Step 4: Create User Groups & App Groups
○ Create user groups based on purpose of service
○ Create app groups based on applications
- Step 5: Configure Your Application
The Application Deployment Wizard helps to publish your application and then verify its status once it is complete.
Akamai EAA is suitable for all applications on a private cloud, an IaaS (such as GCP, Azure or AWS) or an SaaS (such as Office365 or SAP).
Is This for My Business?
● I need to establish a convenient and safe remote access management and a comprehensive auditing.
● I need a simplified partner management and reduce incidents of leakage of information security maintenance.
Service Infrastructure
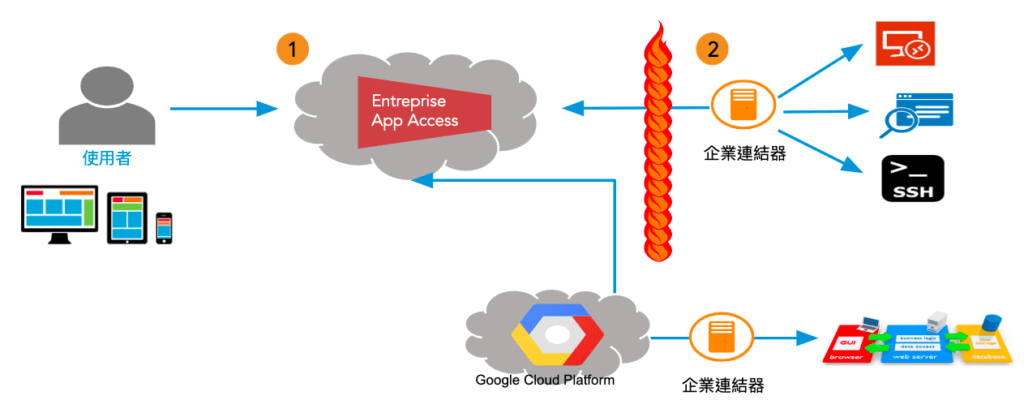
Management edge servers
- Management edge servers:
● Provide security, performance and optimization of components of the digital interface and the data between users and applications.
● Provide features such as management, logging, reporting and settings. Besides a secure, multi-tenant architecture data cloud, you can also choose to have a single-tenant data cloud to deal with the traffic from each single user. - Akamai connectors:
When a user enters the URL in a browser, he/she will be connected to Akamai EAA’s SSO service. He/she only needs to provide a certificate to access applications and integrate with existing SSO products.
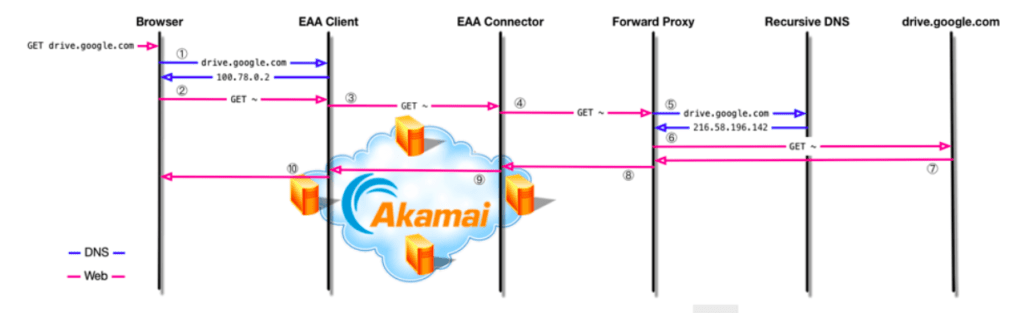
EAA visiting data flow example