Service Overview
Hacking methods change every day. As businesses move most of the data into cloud, Internet threats become a challenge that businesses cannot avoid. Traditional antivirus software and cybersecurity strategies that rely on the release of a virus’s signature are too slow in response. Intrusion Prevention System (IPS) and sandboxes rely on behavioral analysis; yet due to the trend of HTTPS everywhere, hacker attacks also make use of encrypted tunnels to transmit data. It has become more and more difficult to protect against instant attacks.
Akamai Enterprise Threat Protector (ETP) can make up for the lack of defenses. It can actively identify and intercept malware ranging from ransomware, phishing, coin miner malware to the latest and most frequent threats. Akamai ETP provides the most immediate and efficient threat filtering, protection and analysis through its DNS service. It ensures that your users and devices safely connect to the Internet from any location.
Features
- Threats Categorization
Akamai provides the latest intelligence on threats and guarantees a low false alarm rate. The sources of its intelligence include 15-30% of its daily web traffic and 2.2 trillion times of DNS requests and integrated intelligence from other sources.
- Zero-Device Operation
Akamai ETP is a fully cloud-infrastructure solution that can be deployed within minutes so that it will not affect users and services. It can also scale the protection fast without new hardware, which helps to keep your system simple.
- User Behavior Management
Akamai ETP has a built-in and automatically kept list where it categorizes the domains visited by the users. Base on this list, your business can decide which domains to allow or forbid. This can avoid inappropriate visits to porn websites or videos on public devices that can be used by external users.
- Analysis and Reports
Akamai ETP provides your business an analysis of both normal and threatening DNS visits in order to help you understand how your users behave and thus how to control or manage them.
- DNSSEC
You do not have to worry about attacks by DNS man-in-the-middle attacks because all DNS requests that go through Akamai ETP are verified by the DNSSEC mechanism.
Steps of Implementation
- Step 1: Apply for Akamai Enterprise Threat Protector (ETP)
You can get in touch with us here to apply for an Akamai EAA trial.
- Step 2: Configure Akamai ETP Settings
Please provide us your English name, email and phone number so that we can create and set up an account (in the monitor mode) for you on the Akamai portal site. You will receive your Akamai ETP DNS server address.
- Step 3: Point Your DNS Forwarder to Akamai ETP DNS
Your business can delete your existing DNS forwarder setting and point to the DNS server address provided by Akamai ETP. It has no impact on your service to users and will allow Akamai to provide you analysis and reports on your users’ visits.
- Step 4: Deploy Security Connector & Start DNS Redirect and Trapping
Akamai offers you 2 options when it detects an insider threat endpoint visiting your public network. You can choose between activating the blocking mode or deploying a Security Connector VM internally to redirect DNS to the Security Connector while responding with a warning webpage and sending information to Akamai ETP for integrated data analysis.
- Step 5: DNS Behavior Analysis and Control
Akamai ETP offers 16 Acceptable Use Policies (AUP) by default that you can modify to control DNS behavior by categories such as “disable visits to Facebook or YouTube by employees during office hours from 8 am to 5 pm.” Meanwhile, the system records user visits for analysis and control.
Is This for My Business?
- I want to manage user’s usage of the Internet effectively and filter inappropriate searches
- I want to improve the cybersecurity problem that comes with SSL without impacting existing services
- I want to improve the performance of security devices and filter/reduce unnecessary online traffic
Service Architecture
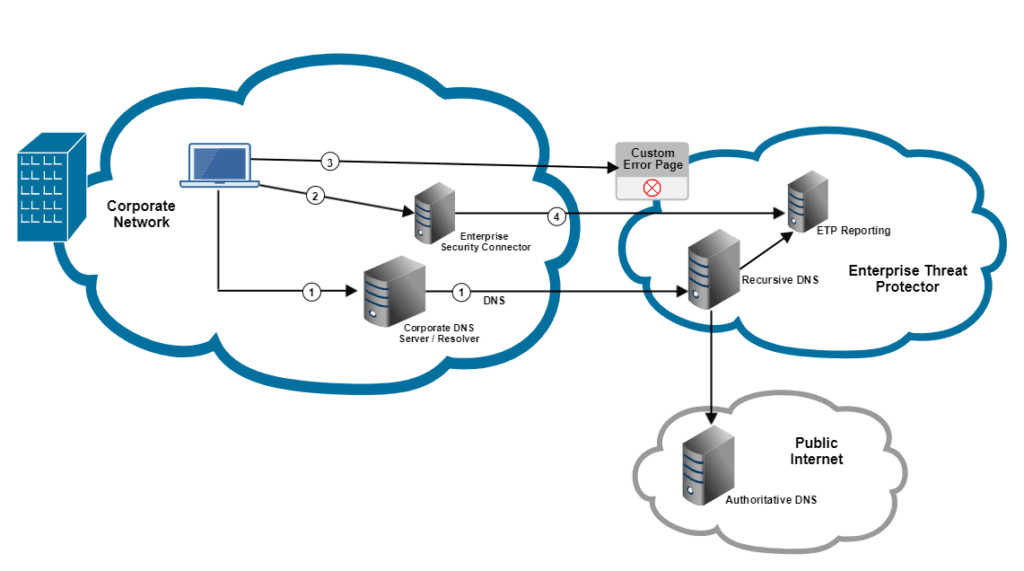
- Point the internal DNS forwarder to Akamai ETP DNS Server
- Deploy a Security Connector VM internally to catch internal threatening endpoints (private IP)
- Activate DNS blocking of threat domain visits on the cloud management platform and redirect such visits to Security Connector to record information about the visits
- Send the threat information gather to Akamai ETP for data association and analysis
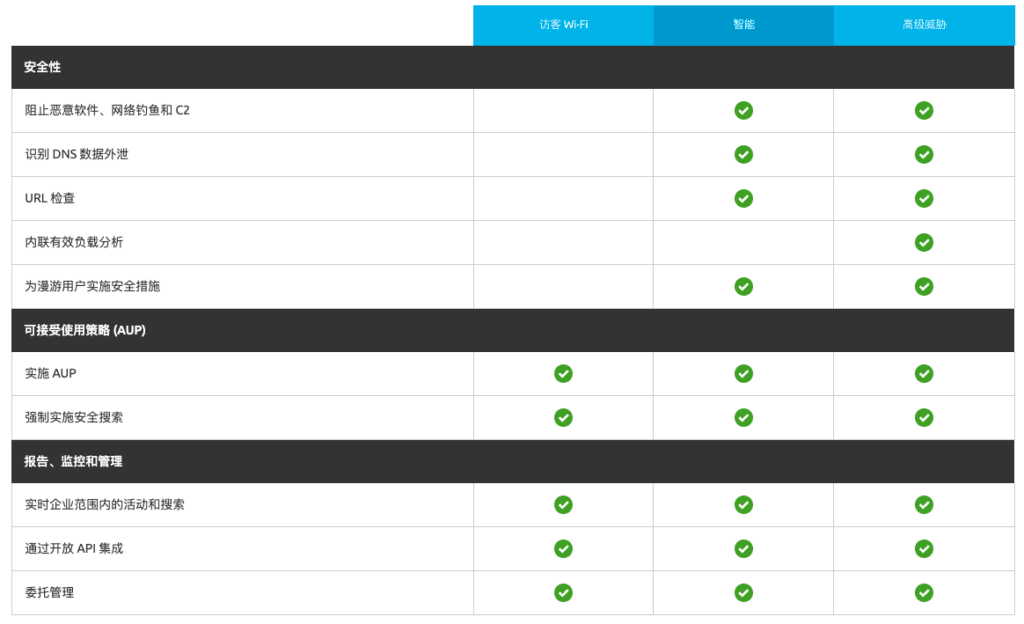
A comparison of different versions