Service Overview
The largest data entry point is emails, which makes it the most vulnerable element in cyber-attacks. Emails have become hackers’ favorite option because of their high targetability and customizability that translate into higher success attack rate. As a result, businesses face more and more junk mails, malwares, and other advanced attacks through emails. The most common advanced types include link to a phishing site, fraudulent requests of wire transfer and weaponized attachments.
Businesses are worried about the more and more attacks through emails that often catch them off guard since emails are critical to operation. Spear phishing, which is directed at a specific business, is especially dangerous because even the most aware employee may accidentally click on the malicious link and expose your business in high risk. In addition, businesses are often too overwhelmed with so many critical parts of the operation that they have no capacity to catch up with prevention of email attacks.
Trend Micro Hosted Email Security offers continuously updated protection against email attacks named above reaching your network. On top of these, it includes an email encryption module that provides an additional layer of protection.
Alternatively, there is FireEye Email Security, which is the most comprehensive email security gateway on the market. It has leading technologies in identifying, insulating and immediate blocking malicious links, business email compromise (BEC), and attacks by attachments. It can integrate with Office365, filter these emails into your junk email folder, and filter outgoing email traffic that might be responding to these attacks.
TrendMicro Hosted Email Security (Basic Solution)
Features
- Against Targeted Attacks
TrendMicro HES uses enhanced protection against social engineering, website credit ratings and the latest detection engines to prevent a targeted attack. In addition, it uses threat analysis technologies in the cloud, exploit detection and simulated sandbox analysis to block targeted attacks.
- Against Social Engineering
TrendMicro HES uses the latest protection against social engineering that cross analyzes each part of an email (e.g. subject, body, delivery information) to identify spears phishing mails.
- Enhanced Credit Rating
TrendMicro HES uses a Smart Protection Network that can scan hyperlinks included in an email and block hyperlinks that point to a malicious website.
- Advanced Threat Scanning Engine
TrendMicro HES uses static and behavioral analysis to detect known zero-day attacks and other abnormalities. It can detect advanced malware inside a document in PDF, MS Office or other formats.
- Simulated Sandbox Environment in Cloud
TrendMicro HES provides a sandbox environment hosted by TremdMicro to deep-simulate email behaviors automatically and to analyze emails with potentially malicious attachments, whether they are executable files or office documents.
FireEye Email Security (Advanced Solution)
Features
● Advanced Simulated Cloud Sandbox Environment
At the core of FireEye ES is an advanced hyperlink protection and FireEye Multi-Vector Virtual Execution (MVX) engine. These technologies use cutting-edge machine learning and analysis to detect attacks that evade traditional signature and policy-based protection.
A critical part of FireEye’s advanced hyperlink protection is PhishVision, an image classification engine. PhishVision has a deep-learning ability to learn from webpage screenshots of trusted and commonly targeted brands so that it can compare against webpages pointed by hyperlinks in emails. PhishVision works with Kraken, a plug-in that detects phishing and trains PhishVision’s deep learning with domain and content analysis. Skyfeed is another innovation used by FireEye ES to detect hyperlinks in emails. Skyfeed is a purpose-built and fully automated system that gathers malware intelligence. It collects social media accounts, blogs, forums and threat feeds to identify misjudgments of FireEye ES. As you can see, FireEye ES is multi-facet and provides its customers with the best protection on the market against credential harvesting and spear-phishing.
● Advanced Anti-Virus & Anti-Spam (AVAS) Protection
FireEye ES provides AVAS protection and detects attacks by using both traditional signature comparison and advanced technologies against business email compromise (BEC, or known as CEO fraud), which will continue to hurt businesses and their finance greatly. BEC attacks do not contain traditional elements such as malware but relies heavily on social engineering. FireEye has developed innovative algorithm, systems and tools that focus on the detection and prevention of BEC attacks.
● Scanning Outgoing Email Traffic
FireEye ES can detect unknown, advanced threats by scanning malicious attachments and phishing hyperlinks in outgoing emails. Meanwhile, it also scans for malware and junk mails in your outgoing email traffic so that your business will not be blacklisted by other businesses.
● Integrate with Notification Workflow
When FireEye ES integrates with other FireEye solutions, we can set up an automatic warning notification workflow for you. FireEye Central Management (CM) can associate notifications from Email Security (ES) and from Network Security (NS) so we may understand attacks better and lay down better blocking policies to prevent an attack from spreading. FireEye Helix also works with Email Security (ES) and is designed to simplify, integrate and automate security tasks.
Steps of Implementation
- Step 1: Open an Account with TrendMicro HES / FireEye ETP
You can reach us here to apply for an account with TrendMicro HES or FireEye ETP.
- tep 2: Set up Mail Relay & Enable Monitoring Mode
We will configure your current mail domain in the email security gateway and set up your identity certificate. This allows the email security gateway to forward safe emails to your mail servers.
- Step 3: Point MX to Email Security Platform through DNS
Next, we need to adjust your mail exchanger (MX) setting through DNS, specifically we will remove your existing MX setting and point to the MX address given by the new email security gateway. This allows detection analysis and control of incoming traffic in the email security platform.
- Step 4: Adjust Setting Based on Email Threat Incident Analysis & Email Security Rules
We will review email threat analysis reports provided by your new email security platform and make appropriate adjustment to your settings. When no major incident is observed after a few days, we will be able to move to the next phase.
- Step 5: Enable Active Protection Mode to Block Potential Emails
In the active protection mode, the email security platform is able to filter threat emails and allows you to configure warning notifications in cases of major threat incidents, which will allow you to take immediate actions against incidents.
Is This for My Business?
● I need to ensure the safety of emails because a large amount of business is communicated & reviewed through emails
● I need to improve the situation of junk mails so my employees can focus on business development
● I need to comply with financial regulations and effectively control the trajectory of threat events
Service Infrastructure
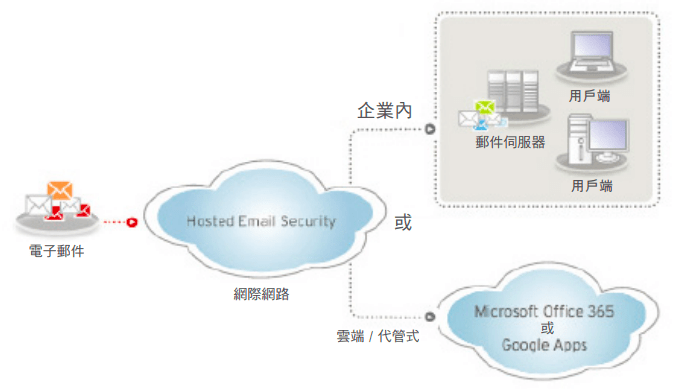
Cloud Framework of TrendMicro HES
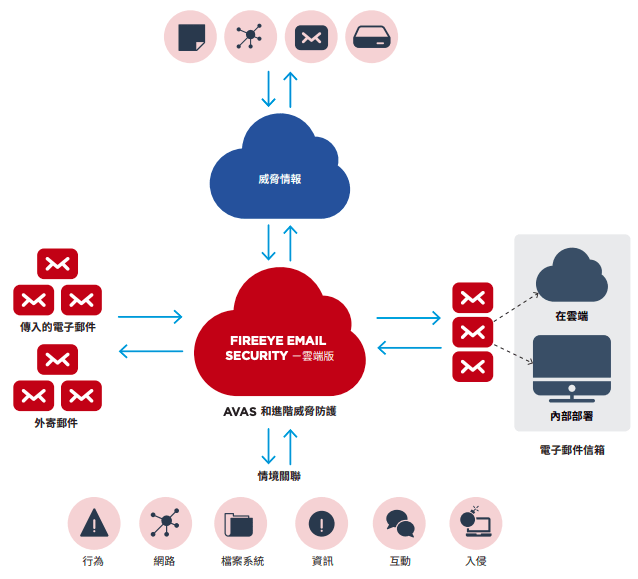
Cloud Framework of FireEye ETP